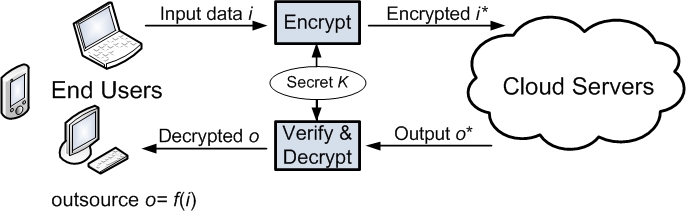
A fundamental concern to move computational workloads from private resources to the cloud is the protection of the confidential data that the computation consumes and produces. Thus, secure computation outsourcing services are in great need to not only protect sensitive workload information but validate the integrity of the computation result. This is, however, a very difficult task due to a number of challenges that have to be met simultaneously. Firstly, such a service has to be practically feasible (immediate practicality) in terms of computational complexity. Secondly, it has to provide sound security guarantee without restricted system assumptions. Thirdly, it also has to enable substantial computational savings at the end-user's side as compared to the amount of the efforts that otherwise has to be committed to solve the problem locally. These challenges practically exclude the applicability of the existing techniques developed in the context of secure multi-party computation and fully homomorphic encryption.
Our research studies secure computation outsourcing in cloud computing with the above challenges in mind. We focus on widely applicable engineering computing and optimization problems. Our methodology is to explicitly decompose computations into public programs and private data and leverage the structures of specific computations for achieving desirable trade-offs among security, efficiency, and practicality. We plan to organize these secure outsourcing mechanisms into a hierarchy, where computation can be represented at various abstraction levels, such that the aforementioned trade-offs can be flexibly explored in a systematic manner. Two critical applications to be studied in this project include secure outsourcing systems of linear equations (LE) [1] and secure outsourcing linear programming (LP) [2] in the cloud. These two applications are among the most widely used algorithmic and computational tools in various engineering disciplines that analyze and optimize real-world systems. The study would prepare a solid knowledge base and provide insights for further research on more advanced computation problems, such as secure outsourcing convex programming in cloud.
