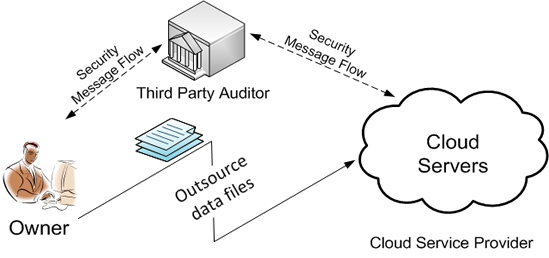
Outsourcing storage into the cloud is economically attractive for the cost and complexity of long-term large-scale data storage. At the same time, though, such a service is also eliminating data owners' ultimate control over the fate of their data, which data owners with high service-level requirements have traditionally anticipated. As owners no longer physically possess their cloud data, previous cryptographic primitives for the purpose of storage correctness protection cannot be adopted, due to their requirement of local data copy for the integrity verification. Besides, the large amount of cloud data and owner's constrained computing capabilities further makes the task of data correctness auditing in a cloud environment expensive and even formidable for individual cloud customers. Therefore, enabling public auditability [1,2,6] for cloud storage is of critical importance so that owners can resort to a specialized third party auditor (TPA) to audit cloud storage services and maintain strong storage correctness guarantee, while saving their own precious computing resources.
Considering TPA might learn unauthorized information through the auditing process, especially from owners' unencrypted cloud data, new privacy-preserving storage auditing solutions are further entailed in the cloud [1,4,5] to eliminate such new data privacy vulnerabilities. Moreover, for practical service deployment, secure cloud storage auditing should maintain the same level of data correctness assurance even under the condition that data is dynamically changing [2,3,6,7], and/or multiple auditing request are performed simultaneously for improved efficiency [1,2,4,5]. Techniques we are investigating/developing for these research tasks include proof of storage, random-masking sampling, sequence-enforced Merkle Hash Tree, and their various extensions/novel combinations.
